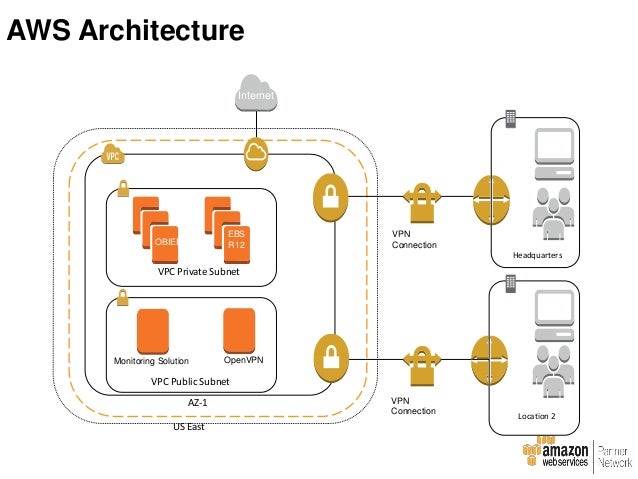
AWS VPC to VPC connections over IPSEC VPN
Learn how to build a secure VPN with security and failover between multiple VPCs using Openswan as a software-based VPN solution. Today, we will be going through how to set up a full-mesh topology (where every region has its own unique connection to all other regions). Openswan is a great choice because first of all it is free to use, and it is quite versatile for different use cases.
Also, if you haven't had a chance to familiarize yourself with Amazon Web Services (AWS) and VPC, I would highly recommend reading up on it. You may be surprised what it can offer your company!
Below this video we provided, configs, and instruction
Also, if you haven't had a chance to familiarize yourself with Amazon Web Services (AWS) and VPC, I would highly recommend reading up on it. You may be surprised what it can offer your company!
Below this video we provided, configs, and instruction
# Install openswan $ sudo su $ yum update -y && yum install openswan -y # Make sure the service start at reboot $ chkconfig ipsec on # Turn on ip forwarding and other needed directives $ vi /etc/sysctl.conf (make sure the these directives are set like what you see below) net.ipv4.ip_forward = 1 net.ipv4.conf.all.accept_redirects = 0 net.ipv4.conf.all.send_redirects = 0 net.ipv4.conf.default.send_redirects = 0 net.ipv4.conf.eth0.send_redirects = 0 net.ipv4.conf.default.accept_redirects = 0 net.ipv4.conf.eth0.accept_redirects = 0 # save the file and apply the changes $ sysctl -p /etc/sysctl.conf # Modify the /etc/ipsec.conf file $ vim /etc/ipsec.conf # Below is the template for what you would set in your connection config. Fill in the brackets with your own info virtual_private=%v4:192.168.0.0/16,%v4:10.0.0.0/8 <---(you can replace these subnets with your own) conn <CONNECTION NAME> authby=secret auto=start type=tunnel left=<LOCAL PRIVATE IP> leftid=<Local PUBLIC IP> leftsubnet=<LOCAL PRIVATE SUBNET> right=<REMOTE PUBLIC IP> rightsubnet=<REMOTE PRIVATE SUBNET> ike=aes256-sha1;modp2048 phase2=esp phase2alg=aes256-sha1;modp2048 # Modify the /etc/ipsec.secrets file with the preshared key you want to use between your peers <Local (LEFT) PUblic IP> <Remote (RIGHT) Public IP>: PSK "mypassword" example: 54.45.58.87 45.65.128.69: PSK "mypassword" You can enable PAT/NAT for your private servers that need internet access by using the following command: iptables --table nat --append POSTROUTING --source <LOCAL PRIVATE VPC CIDR> -j MASQUERADE











No comments
Post a Comment